If your work across a range of customer who add your primary Azure AD account to their Azure AD Tenant as a guest, then you're likely familiar with forcing a resouce to detect and use the correct account.
What Is Managed Identity
Commonly in the Dynamics and Power Platform space we use managed identities to authorize Azure App Services and Azure Web Jobs with Azure Key Vault, to retrieve authentication secrets for connection with Dataverse and external systems that don't support Azure AD authentication.
Let Me Authenticate
The Problem
A common use case is accessing an Azure KeyVault from and Azure App Service. In theory this could cause issues when trying to test an app locally. Thankfull Microsoft document the process of testing locally whith a managed identity. Since local machines don't support managed identity, the Microsoft.Azure.Services.AppAuthentication library uses your developer credentials to run in your local development environment. You can read more here .
While trying to test a Azure App Service Web Job locally in Visual Studio I was not able to force the Web Job to use my account that in linked to Visual Studio. On running the app I failed to retrieve secrets from the target Key Vault.
Following The Docs
The Options
The Microsoft.Azure.Services.AppAuthentication library tries to fetch tokens using the following options in-order:
1. Visual Studio linked accounts ❌
Visual Studio told me to "Re-enter your credentials". Despite doing this multiple times, in multiple ways, the notification would not go away!
2. Azure CLI ✔
Worth investigating.
3. Azure AD ❓
his should work as I'm on a domain joined machine but it isn't (assuming since my Azure AD account is a guest in the target Azure AD tenant)
Option 2 - Azure CLI
To test option 2, I ran the following command in my terminal, which opens an authentication window:
az login
To be sure I target the guest Azure AD tenant I took the following steps:
- Back-out of signing into an existing account:
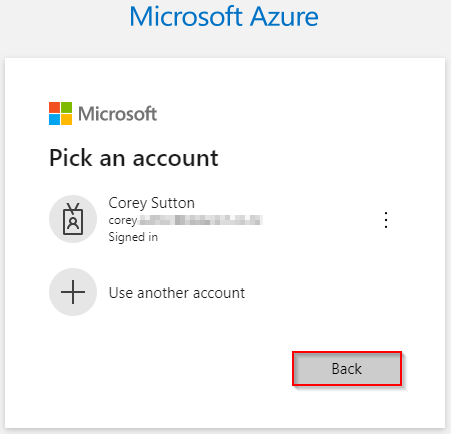
- Click "Sign In Options":
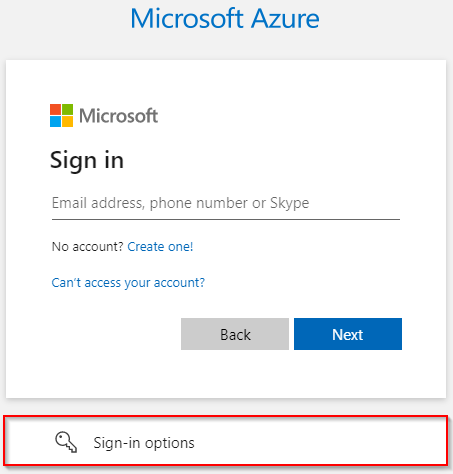
- Select "Sign in to an organization"
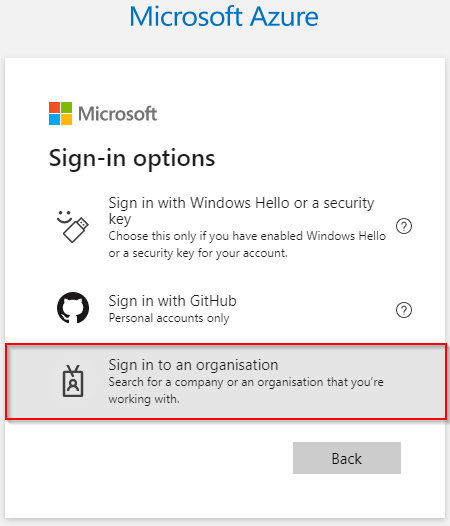
- Enter the domain of the guest Azure AD Tenant:

- From here you can sign in with your account as your would normally. If 2FA is enabled and the guest Azure AD Tenant has a custom bakcground, then you should see this during the 2FA step, rather than the background of your primary Azure AD Tenant.
Conclusion
Now running the app, the correct account is found by the Microsoft.Azure.Services.AppAuthentication library, and the app successfully queries Azure KeyVault and is able to retrieve keys and secrets, and enabled me to test the app locally!
